AWS Lambda Function URLs and Usecases of lambda urls

Learn what is AWS Lambda function urls and how to create a Lambda Function URL
What is AWS Lambda Function URLs?
AWS introduced a new feature to aws lambda called as AWS Lambda function url which are built-in HTTPS endpoints for single-function microservices. This new feature lets to add HTTPS endpoints to any Lambda function and optionally configure Cross-Origin Resource Sharing (CORS) headers without leveraging an api gateway or application load balancer.
This feature enable to use lambda as http end point without using any other aws services like api gateway or application load balancer as shown below,
Similar feature already exists with Google clouse functions and Azure functions for sometimes. Lambda automatically generates a unique URL endpoint and it follows this format:
https://<url-id>.lambda-url.<region>.on.aws
AWS says the <url-id> in the lambda function urls is generated based on multiple factors including the account id and it may be possible for anyone with this info to retrieve the account it from a function url.
How to create AWS Lambda Function URLs from AWS Management Console?
Lambda Function URLs can be added through the AWS Management Console or AWS SDK and is natively suppoted by Lambda APIs. You can also add this feature using infrastructure as code(IaC) tools such as AWS CloudFormation, AWS SAM, or AWS Cloud Development Kit (AWS CDK). For new lambda function, urls can be enabled under the Advanced Settings. For existing lambda function, follow below steps to enable it,
- Navigate to AWS Webconsole and select any existing Lambda
- Click on Configuration tab and you will see a new option as "Function URL - new"
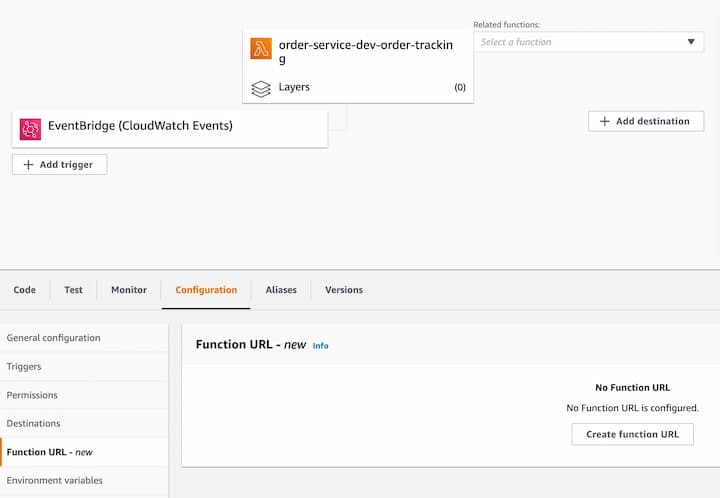
- Click on the create new function url and it will prompt to ask for the authentication type as shown below,
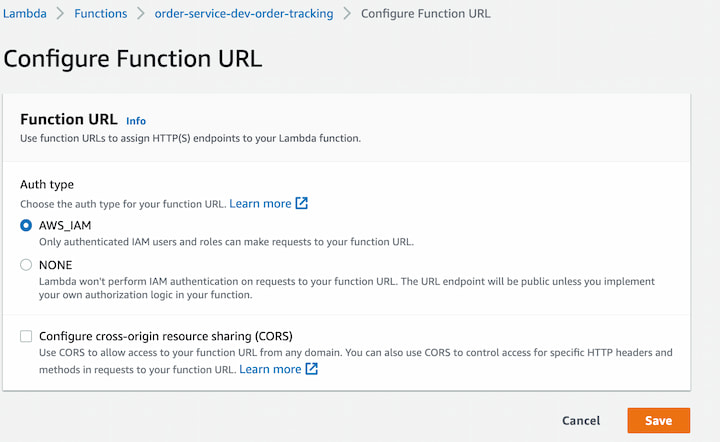
- There are two auth types available now for the lambda function urls.
AWS_IAM: When you set this option, the lambda can be invoked through the function url only when authenticated by an IAM users and roles.The user or the role who invoke the function url should have the permission for lambda:InvokeFunctionUrl on their policy. With this function can be invoked in the same account or cross account as long as the proper permissions are set.
NONE: Auth type is set as public, when the function url need to be public. This allows any unauthenticated user with your function URL can invoke your function. The owner of the function should still have lambda:InvokeFunctionUrl permissions on the resource iam policy in order to successfully invoke your the function URL. Users will get 403 Forbidden error code,if a function's resource-based policy doesn't grant lambda:invokeFunctionUrl permissions even if the function URL uses the NONE auth type.
If the option selected for Auth is None, then console will display the policy allowing access for all users with permission to invoke the function and once it is saved, the policy will be attached to the lambda.
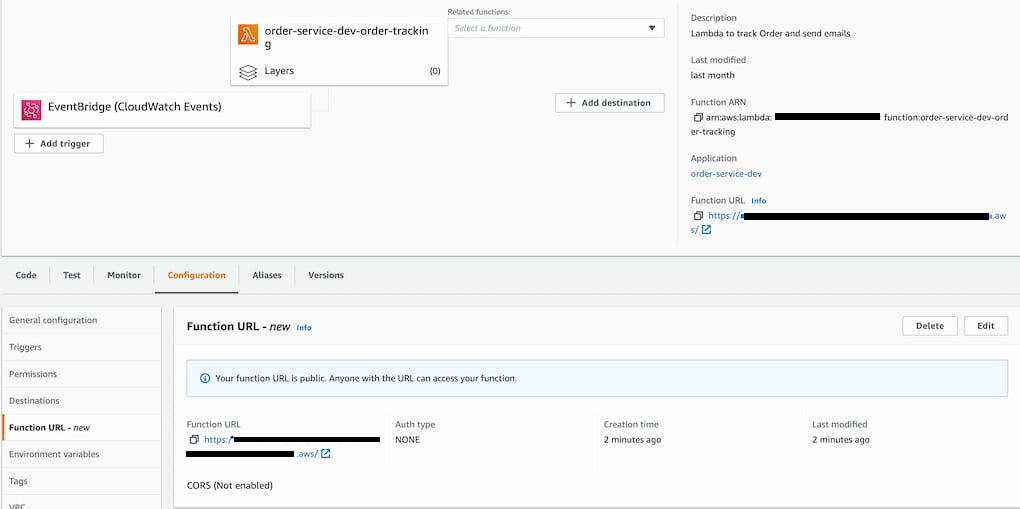
- This should create the function url for the lambda,
Lambda Function URL Request and Response payloads
Lambda function url request and response event payload formats follow the same schema as the Amazon API Gateway payload format version 2.0. Lambda maps the function url request to an event object before passing it to your function and follow the below schema,
{
"version": "2.0",
"routeKey": "$default",
"rawPath": "/my/path",
"rawQueryString": "parameter1=value1¶meter1=value2¶meter2=value",
"cookies": [
"cookie1",
"cookie2"
],
"headers": {
"header1": "value1",
"header2": "value1,value2"
},
"queryStringParameters": {
"parameter1": "value1,value2",
"parameter2": "value"
},
"requestContext": {
"accountId": "123456789012",
"apiId": "<urlid>",
"authentication": null,
"authorizer": {
"iam": {
"accessKey": "AKIA...",
"accountId": "111122223333",
"callerId": "AIDA...",
"cognitoIdentity": null,
"principalOrgId": null,
"userArn": "arn:aws:iam::111122223333:user/example-user",
"userId": "AIDA..."
}
},
"domainName": "<url-id>.lambda-url.us-west-2.on.aws",
"domainPrefix": "<url-id>",
"http": {
"method": "POST",
"path": "/my/path",
"protocol": "HTTP/1.1",
"sourceIp": "123.123.123.123",
"userAgent": "agent"
},
"requestId": "id",
"routeKey": "$default",
"stage": "$default",
"time": "12/Mar/2020:19:03:58 +0000",
"timeEpoch": 1583348638390
},
"body": "Hello from client!",
"pathParameters": null,
"isBase64Encoded": false,
"stageVariables": null
}The function url response payloads is of below format,
{
"statusCode": 201,
"headers": {
"Content-Type": "application/json",
"My-Custom-Header": "Custom Value"
},
"body": "{ \"message\": \"Hello, world!\" }",
"cookies": [
"Cookie_1=Value1; Expires=21 Oct 2021 07:48 GMT",
"Cookie_2=Value2; Max-Age=78000"
],
"isBase64Encoded": false
}Incase lambda returns only valid json , lambda will infers the response format and add,
statusCode is 200,content-type is application/json,body is the function response and isBase64Encoded is false.
Timeout of Function URL
With function url, you get the lambda max timeout of 15min. Compared to API GAteway which is only 30seconds, this is useful incase if the lambda need to be invoked by an http request and processing time is greater than 30 seconds.
Function URL Usecases
Following are a few scenarios where the function url would be great,
- Webhooks where API gateway use case is not required.
- APIs response time is longer than api gateway max response time
- Simple form validator without request validation or cachine.
Lambda Function URLs with Serverless Framework
Lambda function urls are enabled on serverless framework versio 3.12.0 or greater. Function url can be enabled on serverless framework and example yaml configuration looks like this:
functions:
hello:
handler: handler.hello
url: trueServerless Yaml configuration with cors and iam auth type,
functions:
hello:
handler: handler.hello
url:
authorizer: 'aws_iam' # Authorizer used for calls to Lambda URL
cors: # CORS configuration for Lambda URL, can also be defined as `true` with default CORS configuration
allowedOrigins:
- *
allowedHeaders:
- Authorization
allowedMethods:
- GET
allowCredentials: true
exposedResponseHeaders:
- SomeHeader
maxAge: 3600
