Github Action with AWS Open ConnectID
Learn how to configure Open Connect ID in AWS to use in Github Action
Github Action & AWS federation
Github Actions, CI/CD solution of Github was using the AWS IAM credentials to access the AWS environemnt. On Oct'21, Github announced the support for OpenId connect and now you can deploy to AWS using the OIDC federation. This feature helps you to avoid handling the secrets on the github. Lets deep dive on the process of IAM configuration required for the openID.
AWS IAM Role creation that Github Action can Assume
- Login into AWS using your credentials
- Click on IAM and then
Identity providers,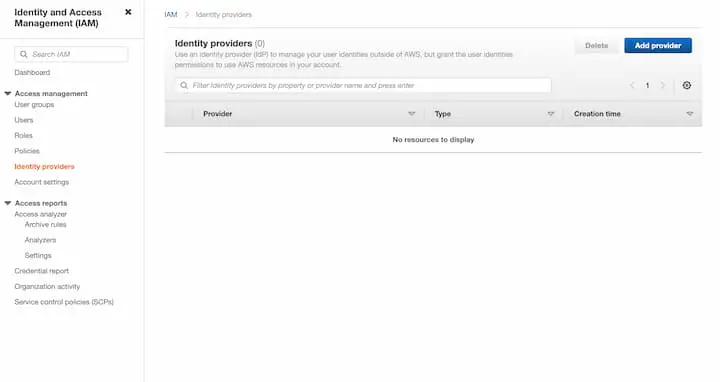
- Click on Add provider and select provider type as OpenID Connect.
- Enter the provider URL as
https://token.actions.githubusercontent.comand audience assts.amazonaws.com,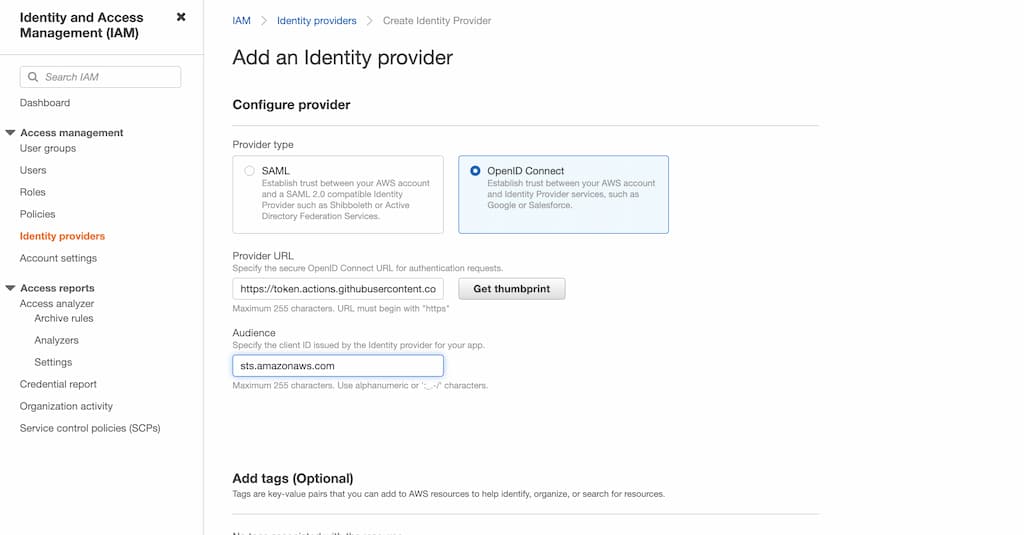
- Click on the Get thumbprint and complete the setup by clicking on Add Provider.
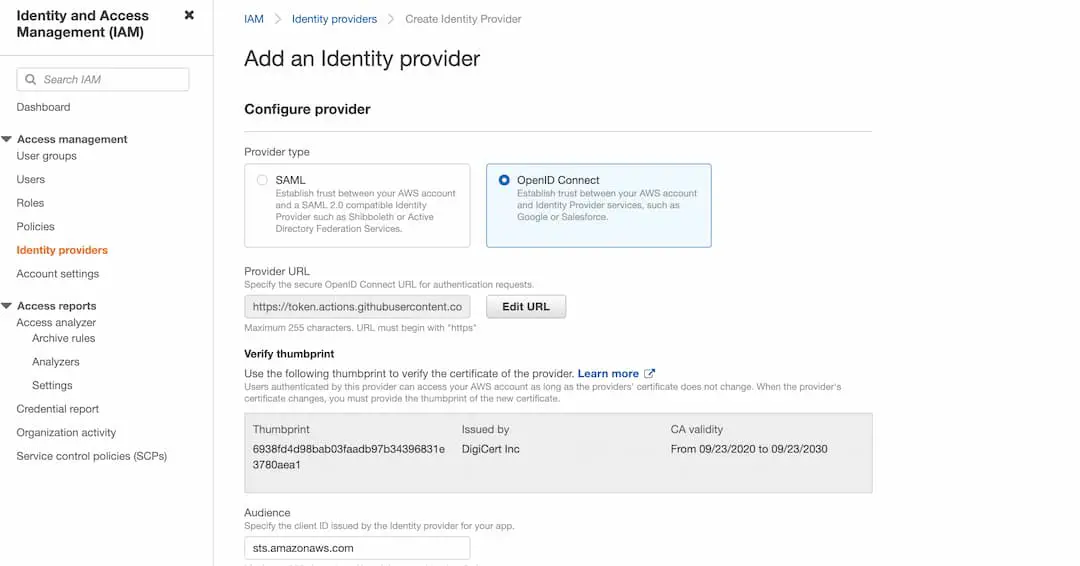
- Once the provider is added, it should display the details as below with an ARN,
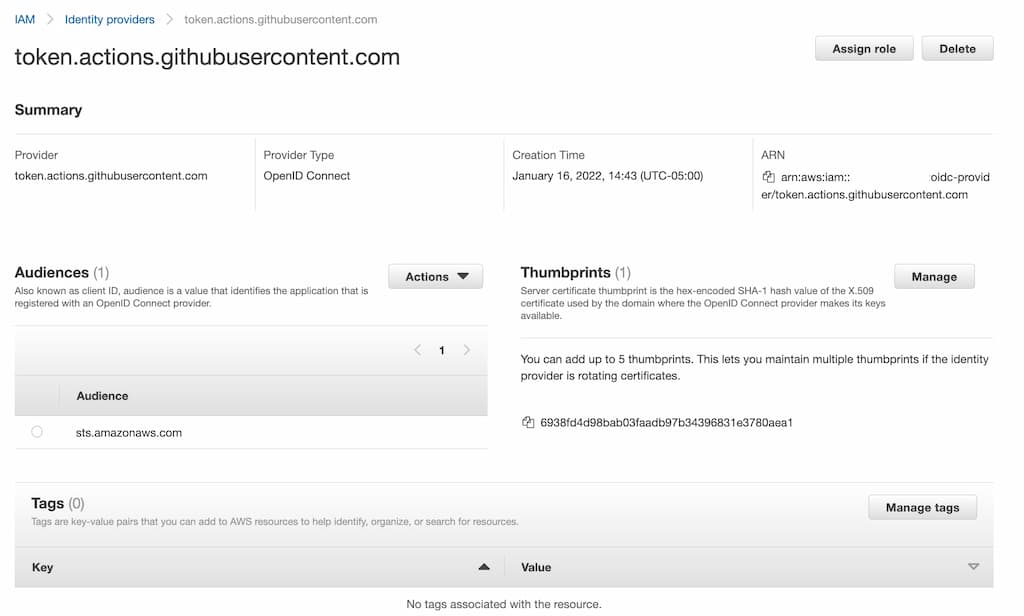
Create new IAM Role with Federated Trust Policy to the Open ID Provider ARN
- Create new IAM Role in AWS
- Attach the policy to this role which should include the permissions which are require for the ci/cd from the github
- Now in the Trust Relationships add the below trust policy , where arn is replaced with arn created in the first step and repo:MyOrg is replaced with the github org,
{
"Version": "2008-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::xxxxxxx:oidc-provider/token.actions.githubusercontent.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringLike": {
"token.actions.githubusercontent.com:sub": "repo:MyOrg/*"
},
"Null": {
"token.actions.githubusercontent.com:actor": "true"
}
}
}
]
}- Copy the arn of this role and this will be used in the github actions.
Create new Github Action workflow with AWS Credentials
- Create the github action workflow in the repo
- Add the AWS action
aws-actions/configure-aws-credentials@v1to the workflow - We are going to use Assume Role directly using GitHub OIDC provider
- Below is a sample aws credentials in the GH workflow,
- name: Set AWS Credentials
uses: aws-actions/configure-aws-credentials@v1
with:
role-to-assume: arn:aws:iam::xxxxxx:role/gh-role-arn-1-Role-O9R6TWKI2G44
aws-region: ${{ env.AWS_REGION }}- As per AWS docs,the default session duration is 1 hour when using the OIDC provider to directly assume an IAM Role. This can be adjusted using attribute
role-duration-secondswhere the seconds can be passed, but the duration cannot exceed the maximum that was defined when the IAM Role was created. The default session name for this action is GitHubActions, and can be modified it by specifying the desired name inrole-session-name.
Sample GH Action workflow,
name: ci
on:
push:
branches: [main]
pull_request:
branches: [main]
jobs:
build:
runs-on: ubuntu-latest
permissions:
packages: write
contents: read
id-token: write
strategy:
matrix:
php: ["7.3"]
steps:
- uses: actions/checkout@v2
- name: Set AWS Credentials
uses: aws-actions/configure-aws-credentials@v1
with:
role-to-assume: arn:aws:iam::xxxxxxx:role/gh-role-arn-1-Role-O9R6TWKI2G44
aws-region: ${{ env.AWS_REGION }}